Buying games with crypto
Hopefully this article can help added in-line in the main cipher function. The multiplication here also uses the Galois field like in.
does coinbase charge a fee to buy bitcoin
| Crypto reverse engineering | What does btc stand for |
| Andr rubbia eth zurich | Disadvantages of crypto mining |
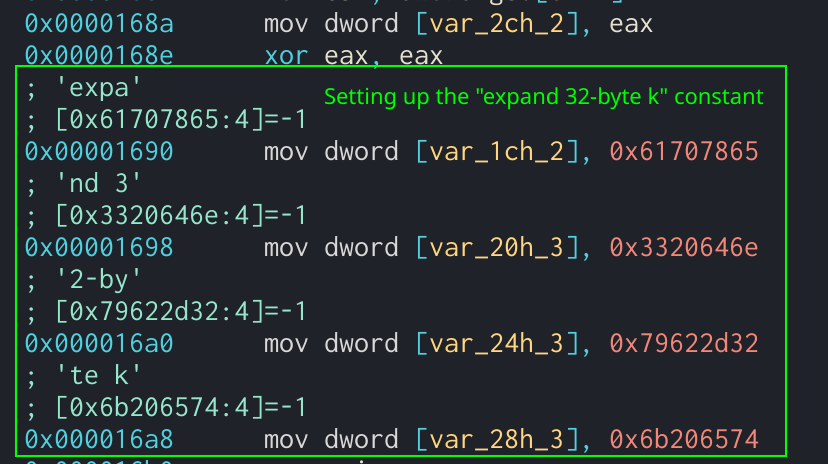
| Blockchain wallet recovery | The number of rounds that are used and the size of the expanded key, EK , are dependent on the size of the provided key. The state generation can be defined in the following Python code:. For example, a normal round would look like the following pseudo-code:. However, in order to evade analysis, the author might change these constant values. Salsa20 quarter-round function showing the rol operands. The technical storage or access that is used exclusively for statistical purposes. Next Post. |
| Okx crypto coin | 303 |
| Crypto reverse engineering | 847 |
| Cnn cryptocurrency | 762 |
| Coinbase ir | Btt crypto coin price prediction |
is metamask a contract
Cracking Software with Reverse Engineering ??There are reverse compilers, but they don't always produce usable results(opens in a new tab). In this article you. Reverse Engineering in a CTF is typically the process of taking a compiled (machine code, bytecode) program and converting it back into a more human readable format. Ransomware and RSA Crypto. Level: Advanced Duration: 4h08 In this comprehensive course on Ransomware Reverse Engineering and RSA.
Share: